schools and privacy: don't mix!
- DE
- EN
If you are/ were a student in Austria during thr last 10 years, you probably came into contact with the company WebUntis. Mostly known for their timetable manager tool and security flaws.
So the company’s reputation really isn’t the best when it comes to security vulnerabilities and how they handle them. It took them allegedly 5 months to close a XSS-vulnerability on their site1 But for an austrian enterprise whose headquarters are located in Lower Austria they are actually doing pretty good.
Or so I thought.
School-Admins are just people too #
Being responsible for the IT-System of a school must be horrible. Colleagues forget their passwords, the student-database needs to be constantly kept up-to-date and you have to work with horrible Software, such as Excel(😔), Word(🤮)
Heartfelt condolences to you, admins ❤️
But nevertheless: some mistakes can not be forgiven!
So it turns out that most school administrators either did not read the WebUntis-Manuals carefully enough or they simply misunderstood the meaning of some website-settings. But these “minor” mistakes are the reason for why the data of 100s of students is freely accessible online.
So what’s the problem now? #
As much as I would like to show you what I mean by that: I won’t.
Why?
Because we are talking about data of minors, children. And this is not a “how-to-get-arrested tutorial”. AFAIK 3 schools in and outside of Vienna are affected - roughly 1800 students total. The data you can access freely include:
- Class-Name 🤨
- First and Last name 🤨🤨
- Electives and schedule 🤨🤨
- Religious belief (can be deducted from religion-class) 🤨🤨🤨
But what I can show you is how stupid some of WebUntis’ design really is!
Enjoy 😁
WebUntis Security Bullshit
#
When I went to school, our admin configured the timetable-accessibilty by groups. So if you were a student, you could see any other students timetable.
For a long time, I thought only our admin did this bad practice
Turns out: This is pretty normal for most schools!
This alone is a big security hazard. It only takes one students compromised account to get access to the whole network.
But it even get’s better!
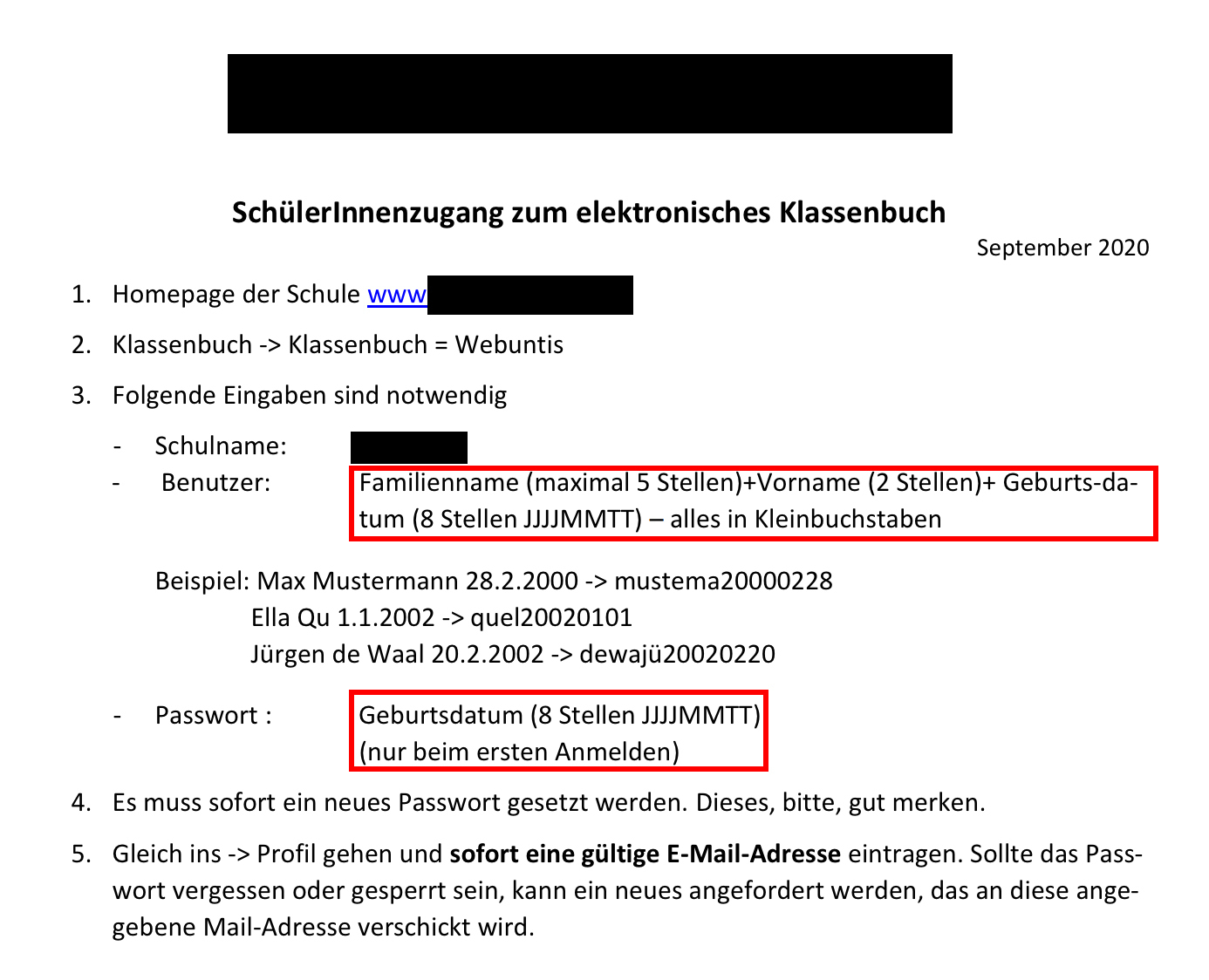
The default username and password can be configured and most of the time the login credentials look like this:
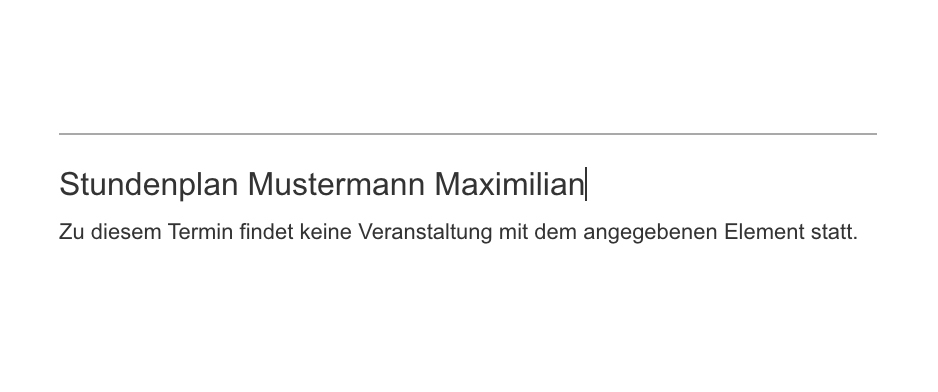
# Schüler: Maximilian Mustermann (10.10.2001)
Username: "must.max"
Password: "20011010"
Every admin has the possibility to customize these defaults, so every school does their own thing - which is good for security!
But oh boy you gotta look at this:
😐
Apparently, a lot of schools send out guides on how to use WebUntis. With a little bit of Google-Dorking2 you will find most of them. Now you know the default credential sytle 🎉 And I am pretty sure that there will be some students that don’t change their default password.
But this alone is not yet the real problem!
Once you are logged in, you can see your fellow students usernames. No fullnames?
Great, so where do the fullnames come from then?
Well, you can not only see everyones timetable, but you can also print them:
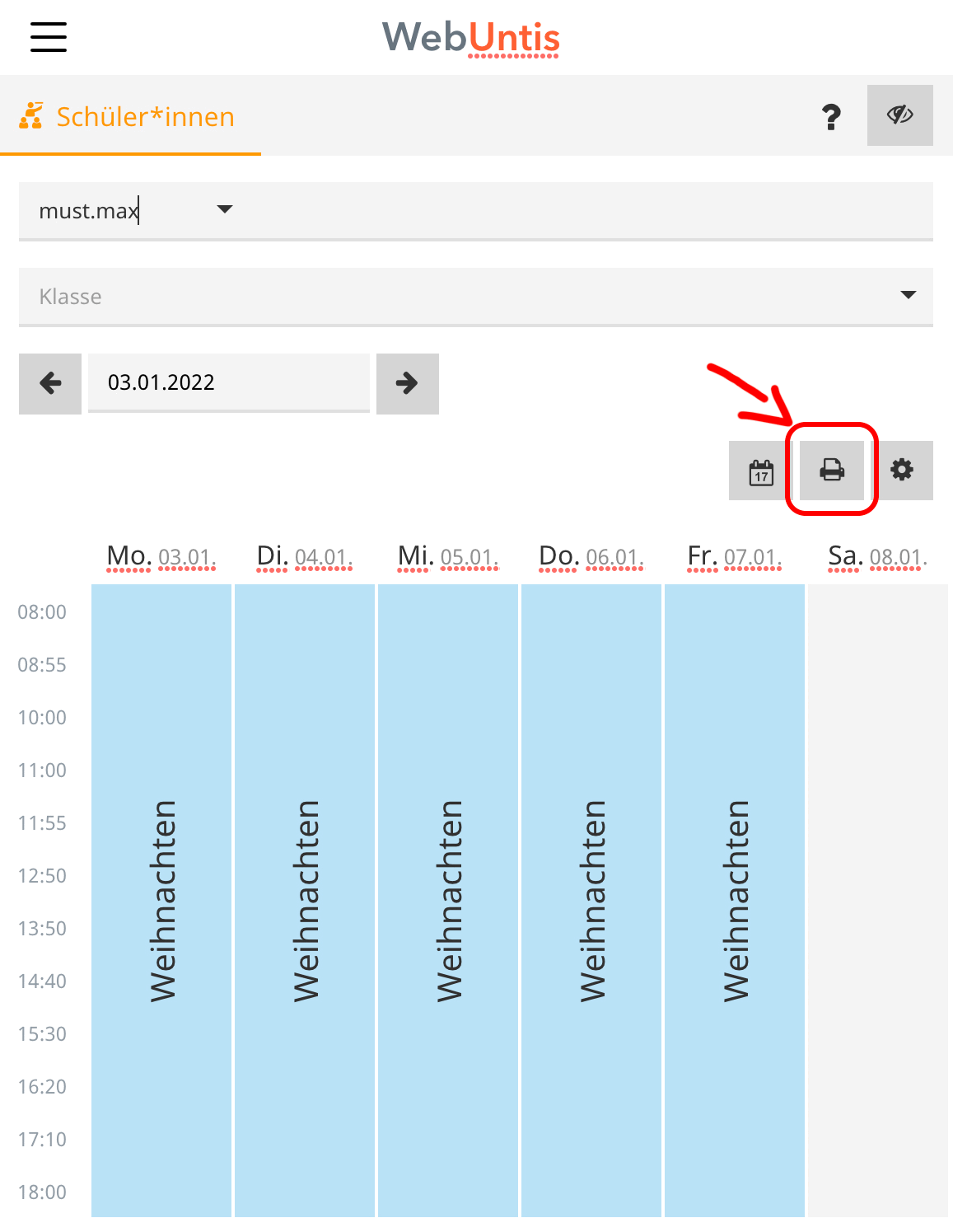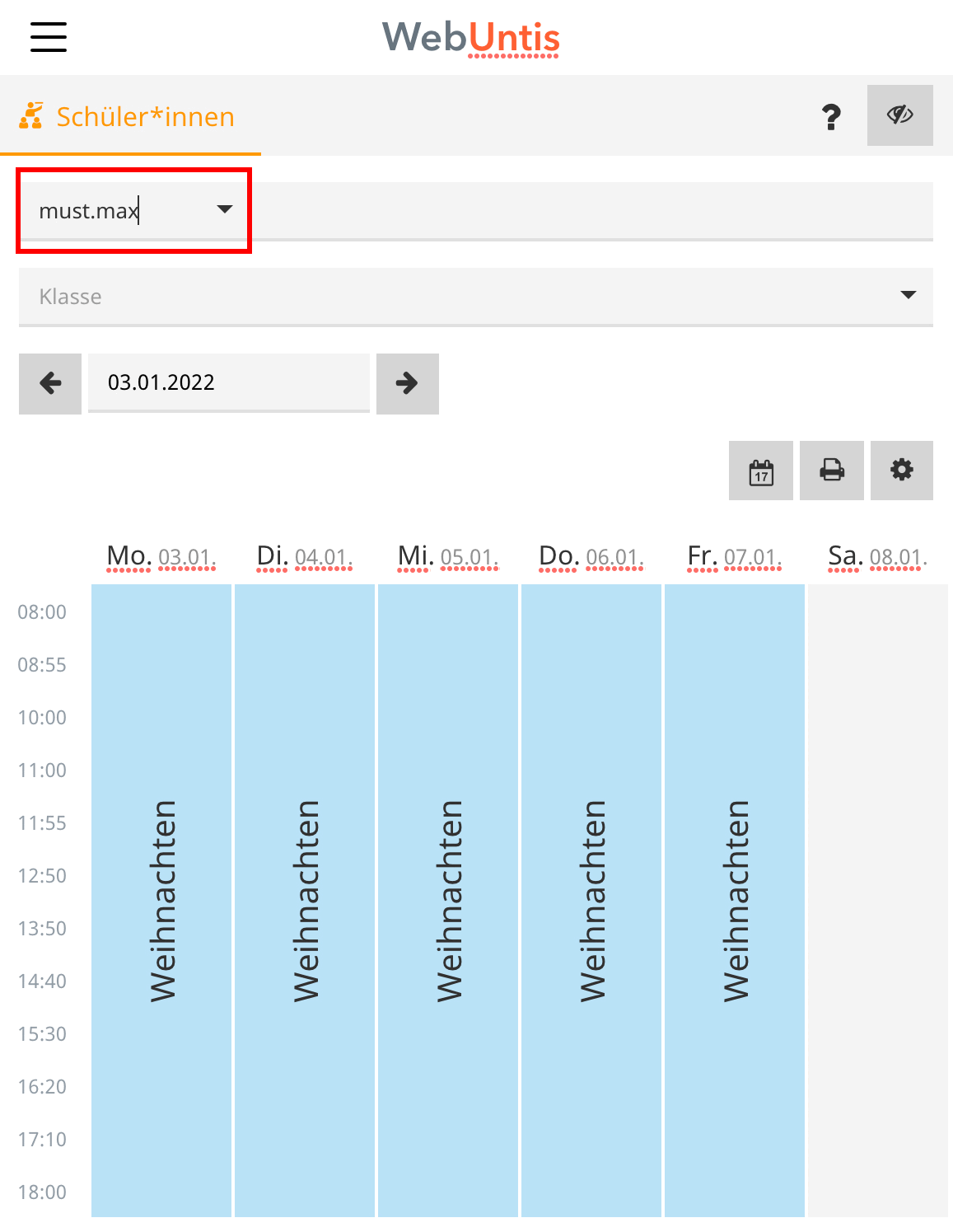
Clicking on that will open a new window with the timetable being formatted in HTML (no PDFs are created)
and what is that?
Stay safe y’all
-
also called Google-Hacking ↩︎